Starting in Firefox 73, users can easily use DNS-over-HTTPS (DoH) and Encrypted Server Name Indication (SNI) for better privacy without extra software. These newer DNS security features help protect user privacy during web activity.
What is DNS-over-HTTPS (DoH)? DoH encrypts DNS traffic with HTTPS (port 443) and HTTP/2 and requires authentication of the requested server.
DNS-over-HTTPS (DoH) or DNS-over-TLS (DoT)? Each handles DNS differently. DoT uses a dedicated port (853) for DNS queries over TLS but doesn’t require the user system to authenticate the requested server. DoT is easy to block because although you won’t see the encrypted traffic, it’s using a dedicated port. DNS-over-HTTPS (DoH) travels alongside other SSL connections and has more support than DNS-over-TLS (DoT). Learn more about why Firefox implemented DoH instead of DoT.
There are cybersecurity and enterprise professionals concerned about whether DoH actually improves internet security and/or adds issues that negate its benefits. Learn more about the concerns with DoH and DoT at SSLStore.com.
DoH can negatively affect the performance of some content delivery networks (CDNs) including Cloudflare and MaxCDN.
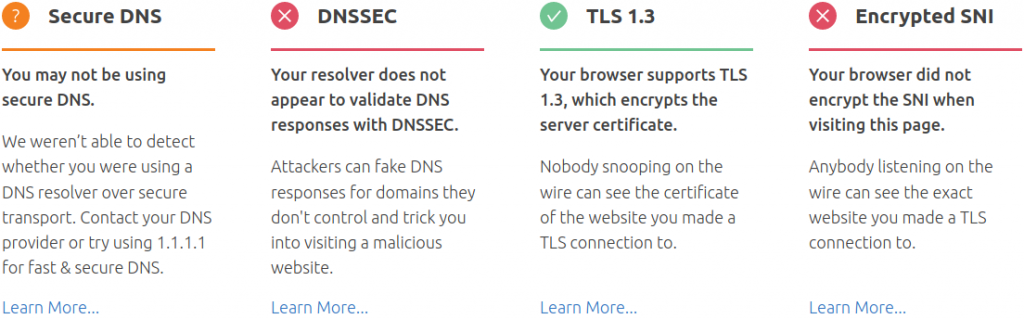
What is Encrypted SNI? The Server Name Indication (SNI) shares the hostname for outgoing TLS connections in plain-text. Encrypting SNI is another way to secure your web activity from man-in-the-middle (MITM) attacks. Encrypted SNI is enabled by default with the Cloudflare DNS resolver.
You should note your current settings before changing anything. Some changes may affect connectivity to your local network resources. Check your internet access after changing each setting to help you troubleshoot any issues you have.
Below, we cover:
DNS-over-HTTPS (DoH)
There are two ways to enable DoH in Firefox:
Preferences Menu
The easiest, preferred option is to use the browser preferences menu.
- Open your Firefox Preferences page
- Under Network Settings, select Settings
- Check Enable DNS over HTTPS
- (Optional) Change your default DNS provider from Cloudflare to NextDNS or Custom (e.g. QuadDNS, Quad101, or another resolver listed in the curl Github page or AdGuard listing)
- Select OK
about:config
For more advanced options, you can edit the Firefox configuration file directly.
- Navigate to
about:config - Type
network.trr.uri - Replace the URI with your preferred DNS resolver
- Select the checkmark icon on the right
Trusted Recursive Resolver
Enabling Trusted Recursive Resolver (TRR) mode affects how Firefox switches between DNS resolvers to improve DNS-over-HTTPS (DoH). This is off by default.
- From
about:config, typenetwork.trr.mode - Select the edit button on the right
- Change the setting to one listed below and select the checkmark on the right
- 0 – TRR off, only native DNS resolving (default)
- 2 – Try TRR first, and use native resolver as a fallback (recommended)
- 3 – Only use TRR, requires bootstrapAddress pref to be set in version 73 and lower; version 74 bootstraps browser using native resolver, unless the DoH server domain can’t be resolved – Bug 1593873 regards portal detection and telemetry (most strict)
- 5 – TRR off by choice, similar to 0 but marked as by choice
Encrypted SNI
- In your browser, navigate to
about:config; - Type
network.security.esni.enabled - Select the toggle button to the right of false to true
DNSSEC
While DoH is DNS encrypted in port 443, DNSSEC is a protocol extension to ensure the query hasn’t suffered from DNS poisoning. Ideally, DNSSEC and DoH would work together to improve user privacy.
There are two sides to DNSSEC support – user-side verification and server-side support.
As an internet user, your internet service provider (ISP) may use DNS Security Extensions (DNSSEC) already. If not, there are ways to use a DNS resolver that does DNSSEC validation:
- Change your router DNS settings
- Install DNS configuration software – e.g. DNS Jumper or DNS-Trigger
- Use a Virtual private network (VPN) – e.g. NordVPN, TunnelBear, and Private Internet Access (PIA)
As a server administrator, you should enable support for DNSSEC on Managed VPS / Dedicated servers or with Cloudflare.
You can test your DNS security settings at Cloudflare.com/ssl/encrypted-sni.
Improve your server security with these 10 ways to harden your VPS. Or enhance your brand with these 5 Web Hosting New Year’s Resolutions for 2020.
