Navigation:
Look at latest visitors in cPanel Setup a cronjob to email WordPress login attempts Blocking unwanted users from WordPress
Because WordPress is such a popular CMS used on the web today, many attackers will try to compromise a WordPress website. Knowing how to review WordPress login attempts in your access logs can help you understand and improve your WordPress security.
This past April there was a large WordPress brute force attack where hackers were trying to hack into many WordPress installs. In this guide we’ll go over how you can be sure that your WordPress site isn’t still getting attacked.
Look at latest visitors in cPanel
To take a quick look to see who has been trying to access your WordPress administration panel, you can simply look in cPanel’s Latest Visitors tool following these steps:
- Login to cPanel
Under the Metrics section, click on Latest Visitors
Beside your WordPress domain, click on View
Type in wp-login.php into the search box with the magnifying glass
Then click the Settings cog on the right, and place a check beside the IP, URL,Time,Status, and Method fields.
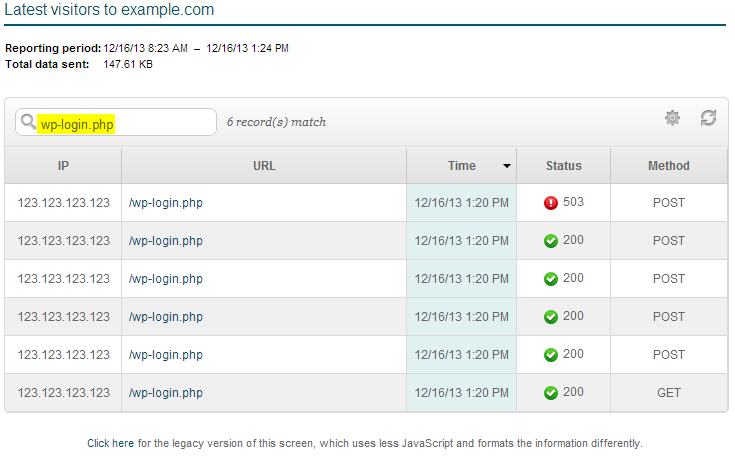
Here you can see that the IP address 123.123.123.123 first had a GET request for the wp-login.php script, followed by 4 POST attempts, all getting a 200 response.
On the 5th POST attempt the login was blocked and given a 503 response, and this is an indication of a user attemping to login to your WordPress admin, continually failing, and then being blocked by our Mod Security rules on the server.
You might also see that you have a ton of different IP addresses trying to hit your wp-login.php script here as well, and at a much higher volume. If you’re seeing this, then that means your site could still be under a WordPress brute force attack.
Setup a cronjob to email WordPress login attempts
A lot of times you might not be reviewing your WordPress website on a daily basis. In these cases it can be helpful to setup a cronjob to send you a daily report of any attempted WordPress logins following these steps:
- Login to cPanel
Under the Advanced section, click on Cron jobs
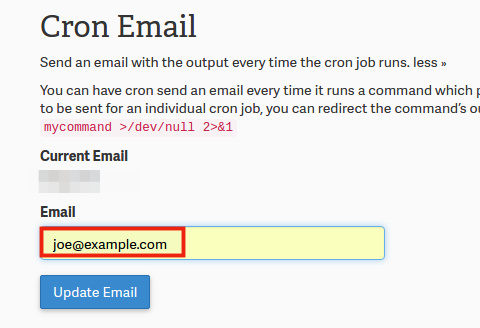
Under the Cron Email section, fill out your email address where you’d like to receive the daily WordPress login attempt reports, and click Update Email
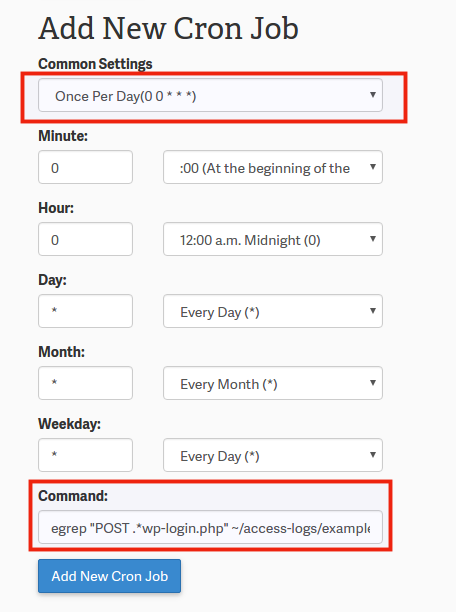
Now under the Add New Cron Job section, change the Common Settings drop-down to be Once a day (0 0 * * *)
This will default to sending you an email at midnight local server time, but you can adjust the Hour field if you’d like to have it email you a different time of day.
Now for the Command field, you’d want to enter in the following command, making sure to replace ~/access-logs/example.com with your own WordPress website’s log:
egrep “POST .*wp-login.php” ~/access-logs/example.com | awk ‘{print $1,$4,$5,$6,$7,substr($0, index($0,$12))}’ | awk ‘{print $1}’ | sort -n | uniq -c | sort -n | sed ‘s/[ ]*//’
Then click on Add New Cron Job
- The email report will give you a list of IP addresses that were accessing your wp-login.php script, and how many times they did so, and look like this:
30 58.10.130.202 30 78.164.24.100 31 223.207.219.14 32 171.101.134.230 32 171.5.251.198 32 223.204.248.61 32 88.12.44.113 33 49.49.168.61 36 223.205.123.216 60 95.135.187.135 100 61.109.125.146
In this case if we received an email report like above, we can clearly see that we possibly have a brute force attack happening on our WordPress sites, as we have multiple IPs hitting the wp-login.php script multiple times.
Blocking unwanted users from WordPress
If you notice that you have IP addresses trying to access your WordPress admin that shouldn’t be, you can go ahead and block unwanted users from your site using .htaccess.
In the example email report above we saw multiple IPs had multiple login attempts, we can block these IPs from even being able to send out website a request by using these .htaccess rules at the top of your .htaccess file:
deny from 58.10.130.202 deny from 78.164.24.100 deny from 223.207.219.14 deny from 171.101.134.230 deny from 171.5.251.198 deny from 223.204.248.61 deny from 88.12.44.113 deny from 49.49.168.61 deny from 223.205.123.216 deny from 95.135.187.135 deny from 61.109.125.146
Now if any of these IPs trys to access your website again, they will be immediately given a 403 access denied error and won’t be able to attempt to login to your WordPress site any longer.


Instead I got this error messagin in mail:
/bin/bash: -c: line 0: syntax error near unexpected token `(‘
/bin/bash: -c: line 0: `egrep “POST .*wp-login.php” ~/access-logs/lamyig.net | awk ‘{print $1,$4,$5,$6,$7,substr($0, index($0,$12))}’ | awk ‘{print $1}’ | sort -n | uniq -c | sort -n | sed ‘s/[ ]*//’’
Hello Dawa, sorry that you’re running into trouble. In the sample you posted, it looks like you need to use the standard quotation marks
"instead of the smartquotes like“. Same goes for the single quotes'. BASH scripts are really picky about that sort of thing. Hope that works!Excellent and useful, but gosh…the size if the images!
Sorry about those image issues! We’ve been updating many of our articles after changing some display options and some of the images are still displaying smaller than we’d prefer. For now, you should be able to open the images in a new tab and see them at a more appropriate size. I’ll make sure this one gets added to the update queue. Thank you for pointing it out!
nice one
Nice one, I was supprised this morning to know my wordpress login page has been disabled, I will try these right away
Sorry to see that. Let us know if you have any questions regarding the process!
I just received a message that I’ve been blocked from my WordPress blog account due to a brute force attack. How long will I be blocked for, what do I/can I do, and how do I ensure this won’t happen again? Or have I lost my blog permanently…
If it states Temporarily Disabled, please follow this guide for options.
Hi, I have a few blogs all in one domain under different sub domain. My site has been under a series of very consistent Brute Force attack this week which brought down the server time and again. I have allowed wp-login.php access only to my ip and deny all others. However, my question is, how do I know if I entered the right code in .htaccess file? And how do I know if I have successfully denied all other IPs accessed?
A sample of what I enter into the .htaccess file:
<filematch “^(xmlrpc|wp-login)\.php$>
allow from ip1
deny from all
</filematch>
It seemed that after making this entry, when I tried to access the file, I just get 404 not found error.
You will want to set up the allow/deny for IPs in this order to allow only one IP through.
order deny,allow
deny from all
allow from <your ip>
As a newbie trying several times to login and failing (until I got spoke with tech support). Then receiving a Brute Force prompt and reading the following day your post of “Reviewing WordPress Login Attempts”, I was wondering if it was my attempts or my VPN running in the background. Or both.
The server looks for any attempts to log in, so those could come from anywhere. Largely, if it happens a lot, it is due to outside sites trying to force their way in.
i try the following but it give me the following error in the email message :
output : egrep: /home/webmec6/access-logs/mydomain.com: No such file or directory
PLease advice !
When I send into my wordpress website I can’t see the dashboard. This is over 6 days and now and when I insist I get a 404 error page from Hostgator; how do I rectify it?
Hello Emily,
Sorry to hear that you’re having problems with the login. If you are hosting with HostGator, then you will need to contact their support if you continue to have repeated login issues. If you are using our hosting service, please provide a URL for your site and we can investigate further.
If you have any further questions or comments, please let us know.
Kindest regards,
Arnel C.
Is it possible to whitelist an ip or two so that they can get through when a block happens? The primary administrator shouldn’t get locked out during this period of time.
Hello Dan,
The block happens at the mod_security level, so that is an all or nothing toggle. You can contact Live Support to have that rule disabled if you like, but you are basically whitelisting everyone.
Kindest Regards,
Scott M
The block happens at the mod_security level, so that is an all or nothing toggle. You can contact Live Support to have that rule disabled if you like, but you are basically whitelisting everyone.
I have just paid for a month subscription and cannot sign in. It says that I’m blocked. What do I do?
Hello Brande,
This is just a public forum. Please, contact our Live Support team. They are available 24/7, 365 days a year.
Thank you,
John-Paul
I am receiving database error messages when will this issue be resolved?
Hello Felipe,
Sorry for the database errors that you’re seeing. Can you please give us some details, as we’re not seeing anything on your website at this point. If you are still having the problem and require technical assistance, please provide more detail on the exact error message, and also how to duplicate the problem.
Regards,
Arnel C.
Hii,
I am facing a problem to login in my WordPress admin panel … When I open my WordPress admin panel page it show me nothing, just a message
LockeD By MED
pass plz:
Please help me to get rid out of this ..
Thanks in advance
Regards
Lisa
Hello Lisa,
Doing a Google search for LockeD By MED and WordPress, it seems like this could be an indication of your WordPress website being hacked.
I was unable to find any account information for you in our system based off the email address you submitted this comment under. But I might recommend you take a look at my guide on how to reinstall WordPress after a hack to see about possibly getting this hack cleaned up from your site and allow yourself back into the WordPress admin section.
You might wish to also contact your web host directly and let them know about these issues so that they can take a look on the server and in your WordPress database for any signs of malicious activity or a possible hack.
– Jacob
Wordfence is a pretty good plugin for defeating Brute Force attacks…
Hello Peter,
Yes the WordFence plugin in one of many WordPress security plugins that can help with WordPress brute force attacks.
Thanks for your comment!
– Jacob
How can I stop this web site from being blocked my web site is time sensitive
Hello Peter,
If you are being blocked from accessing your website admin area, you will want to perform the steps included in our WordPress brute force article.
If your site is being suspended by our Systems team, you will want to contact our Live Support team to investigate the cause.
Kindest Regards,
Scott M
Actually, as you can see in the logs there is ONE POST request. One intial GET request for wp-login.php The remaining are GET requests. In other words, GET requests from the referring page wp-login.php, as I already pointed out.
Why is this a new comment btw… It was supposed to a reply to JacobIMH in the thread we started above.
Hello Jim,
I just tested again and this time I also got our ModSecurity block on your WordPress site.
I went ahead and disabled specfic ModSecurity rules dealing with our WordPress brute force protection, so that your site is still protected from other types of attacks.
Being that our protection is disabled for your WordPress site, you’ll want to be sure that you follow the steps from our WordPress brute force guide to help protect your WordPress installation from attackers.
Please let us know if you’re still having any issues at all.
– Jacob
Yes. The logs only show 7 requests, first landing on wp-login.php and 4 for its respective css files and one for the log. The seventh entry is the POST to wp-login.php. Every first attempt results in the white page saying login has been delayed. We are not being brute forced attacked, yet we are locked out because somewhere a rule thinks so.
Thanks!
Jim
As you can see from these logs, there are several POST requests to your wp-login within just a couple seconds which if they are failed logins, will certainly block access to your WordPress admin. I recommend fully protecting it with your .htaccess file.
Jim is referring to our VPS hosting account.
I do prefer the domains be kept private, as it’s development site not for public consumption.
Thanks,
Stephen
Hello Jim and Steven,
I’m not seeing any issues when I try to login to the WordPress site that you’ve mentioned privately.
When you say that you are getting blocked out the first login attempt every time, are you getting redirected to an all white error page that has a link to our article about the WordPress brute force attacks, or something else?
I do not see any mention of the Mod Security rule we use to block WordPress login attempts in your Apache error logs. So it looks like you might be having a completely separate issue.
– Jacob
I think there’s something wrong with the rule to block. I just installed WP. I keep get blocked out on the first login attempt every time.
Thanks
Hello Jim,
The block rule should work as described. You may want to have us check your individual account to see that everything is implemented properly. You may want to reply with your domain name here. We can keep it from being public if you prefer.
Kindest Regards,
Scott M
I locked myself out of mysite trying to access wordpress. Do I have to wait for it to reset or is it someting I can change inside of inmotion.
Hello Rafaael,
If you had too many incorrect WordPress login attempts then you would have triggered our WordPress brute force attack security rules. If this is the case, you could wait a full 15 minutes before attempting to login again, and then it should let you back in as normal.
Please note that during that time, if you have other users also trying to login to WordPress this could extend the 15 minute temporary block. In which case you’d want to use one of the methods described in that guide for limiting access to the WordPress admin section such as setting up a secondary WordPress password.
If you’re still having issues logging in after waiting a full 15 minutes before trying again, please let us know.
– Jacob