After downloading a file, it’s always helpful to validate it to ensure its not corrupt or malicous. You can accomplish this by comparing checksums – md5sum, sha1, sha256, sha512, etc. – against the original file if its published on the official website. You can use your computer, SSH, and websites such as VirusTotal.com to achieve this. Below we’ll demonstrate how to do this using SSH with a manual download of WordPress 4.9.8.
Note: The higher the number in the algorithm – sha224, sha384, etc. – the stronger the authentication process. Also, this along with the larger the file being validated determines the time before validation completes.
Warning: Verifying the checksum against the website only checks that it wasn’t corrupted during the download. It doesn’t guarantee the file isn’t malicious. If the website is hacked, the checksum could also be modified to that of the malicious file. If you believe you may have malicious content on your server, please request a free server scan and review our hack recovery guide.
Verify Checksum with SSH
- Upload the file(s) into the correct directory.
- SSH into the cPanel account using the correct steps for your hosting plan – Shared or VPS/Dedicated.
- Type the preferred checksum command and the path to the file –
e.g.md5sum file.jpgorsha1sum public_html/file.png.
For example, here’s the md5sum and sha1sum output for the downloaded WordPress 4.9.8:
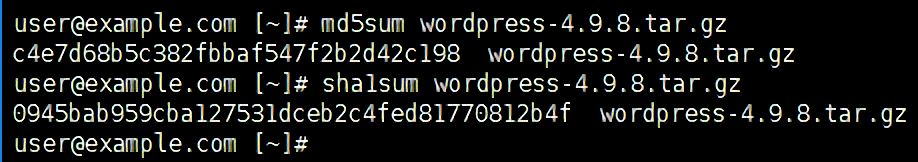
- Check that the checksum(s) match the original file. Both checksums above match the md5 and sha1 checksum respectively from WordPress.org.
If your SSH checksum matches what’s on the official site, congratulations. If not, you may want to try another validation program (e.g. GtkHash) or method of downloading the original file such as from a reputable location.

This sounds like the process for confirming validity of a program. What when you are downloading several hundred pages of your own website? Are you suggesting checking each de-compressed file separately? (One of your many help files specifically says that the download tar.gz tarball must be decompressed before it is used uploaded to the new server.
Good question, John. I’m going to go over a few points I think will help, but I wanted to link you to our article on the best practices for using checksums because I think that covers a lot of the relevant material.
You may benefit from using checksums to verify data integrity of files on your server – if you’re concerned about file corruption or data loss or something like that, there are use cases where it may be useful to check those files — or at least the tar.gz file. Usually though, when we talk about checksums in this context we’re talking about verifying downloaded files from public facing sites or third party downloaders. Those can end up with corrupted data entirely independent of any security concern.
If you’re concerned about malicious data or hacked install files, your best bet is to use an anti-virus scanner coupled with something like publicly available sites like the scanner on virustotal.com to make sure you’re getting what you expect.
Lastly, remember that checksums just verify file integrity. If you’re verifying the file integrity of something downloaded from a hacked/malicious source, the checksum can be 100% ok even if the file itself is dangerous. Checksums are just another tool in the toolbox; they have security and data applications, but only as part of a broadly applied toolset. I hope that helped to provide more context.