On April 7th, 2014, a very alarming security flaw was exposed in multiple versions of OpenSSL 1.0.1 – 1.0.1f.
OpenSSL is the open source software responsible for implementing SSL and TLS encryption and decryption for a large number of websites on the Internet.
This vulnerability has been deemed the Heartbleed bug named after the client/server heartbeat feature introduced in OpenSSL 1.0.1 that is exploitable.
The Apache and NGINX web servers that use OpenSSL by default, account for some 66% of all website traffic on the Internet. There have already been confirmations of over 500,000 widely trusted websites being affected.
The Heartbleed bug can expose 64kb chunks of sensitive data to an attacker from a server’s memory. This can include passwords, credit card info, emails and more, and is why this is a very large security risk.
InMotion Hosting customers, we’ve already patched all vunerable versions of OpenSSL on our network.
We released a news update about the Heartbleed 0-day exploit when we first found out about this issue.
Offical OpenSSL vulnerability disclosure
The official CVE or Common Vulnerabilities and Exposures notice, is CVE-2014-0160 for this OpenSSL exploit.
This is a memory buffer exploit, and it was reported on the OpenSSL website affecting versions 1.0.1 – 1.0.1f.
OpenSSL CVE-2014-0160
CVE-2014-0160: 7th April 2014
A missing bounds check in the handling of the TLS heartbeat extension can be used to reveal up to 64kB of memory to a connected client or server. This issue did not affect versions of OpenSSL prior to 1.0.1.
Fixed in OpenSSL 1.0.1g (Affected 1.0.1f, 1.0.1e, 1.0.1d, 1.0.1c, 1.0.1b, 1.0.1a, 1.0.1)
Vulnerable versions of OpenSSL with TLS/TTLS heartbeat support
| openssl 1.0.1 | openssl 1.0.1:beta1 | openssl 1.0.1:beta2 | openssl 1.0.1:beta3 | openssl 1.0.1:a |
| openssl 1.0.1:b | openssl 1.0.1:c | openssl 1.0.1:d | openssl 1.0.1:e | openssl 1.0.1:f |
Checking for OpenSSL Heartbleed bug
It’s important to point out that OpenSSL itself is not vulnerable. Only the Heartbeat feature, developed back in December of 2011, and then released in the OpenSSL 1.0.1 release branch on March 14th 2012 introduced the bug.
Checking for the OpenSSL Heartbleed bug
You can very easily check the version of OpenSSL you’re running on your server with a simple phpinfo() check. Simply create a PHP script called info.php with this code in it:
<?php phpinfo(); ?>
Access that script at https://example.com/info.php, then in your browser hit Ctrl-F and search for openssl:
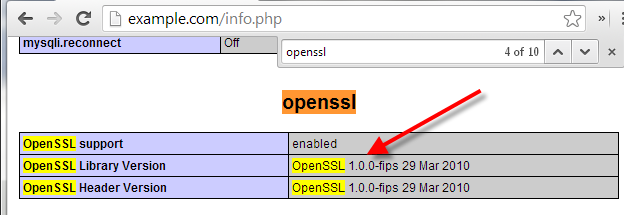
In the screen shot above, you can see this server is running OpenSSL 1.0.0 which means it has not been updated to include heartbeat support, which means it is not vunerable to the heartbleed bug.
REMOVE the info.php script after looking at it for security purposes.
If vunerable version of OpenSSL found, check for patches
You need to have root access on your server to check the OpenSSL changelog for applied patches.
A common command to check your OpenSSL changelog is:
rpm -q openssl && rpm -q –changelog openssl | head -10
If your vunerable version of OpenSSL has been successfully patched, then you should see something like this:
openssl-1.0.1e-16.el6_5.7.x86_64 * Mon Apr 07 2014 Tomáš Mráz <[email protected]> 1.0.1e-16.7 - fix CVE-2014-0160 - information disclosure in TLS heartbeat extension * Tue Jan 07 2014 Tomáš Mráz <[email protected]> 1.0.1e-16.4 - fix CVE-2013-4353 - Invalid TLS handshake crash
If you do not see the recent CVE-2014-0160 patch applied to your version of OpenSSL, and you’re running one of the vunerable 1.0.1 versions, you should have your host upgrade right away.
Security risks of OpenSSL heartbeat exploit
Unfortunately there is a large security risk due to this exploit because a lot of trust is given to SSL or Secure Socket Layer connections on the Internet these days.
This is because even if an attacker is sitting between a client and server looking at Internet traffic, when using a SSL connection, all information transmitted is expected to be encrypted and unviewable to anyone.
Best security practices moving forward
There has been a list of sites that were affected by the Heartbleed bug put together by Mashable in their Heartbleed hitlist. Some big players like FaceBook, Instagram, Pinterest, Tumblr, Google, Yahoo, DropBox, OKCupid, SoundCloud, and more could have been affected.
It’s highly recomended due to the possibly security implications of this exploit that all Internet users update all of their online account passwords. You should consider using a strong password for all of your accounts, and possibly storing them in a secure password safe.
Some common critical private information that relies on hiding behind secure encryption is but not limited to:
- Authentication ( usernames / passwords )
- Credit Card / Financial data
- Private conversations
- SSL private keys

totally agree, this needs to be mentioned, Apache restart worked for me too ! thanks inmotion !
The website https://filippo.io/Heartbleed/ which is a commonly used tool for checking for the Heartbleed bug, was reporting our site as “vulnerable”. This was after InMotion applied their patch, etc. It was not until I manually restarted Apache and SSH on my server that filippo.io said the issue was “fixed” on our site. Just an FYI to others who might have the same issue.
Hello Michael,
Thank you for your comment. You are correct, at times it does require an Apache service reset. We will ensure that information is included.
Kindest Regards,
Scott M