If you’ve read our previous article on how to pass PCI compliance scans, you might have recently failed a PCI scan and are curious about what needs to be done to pass. One of the most common PCI compliance requirements for passing a PCI scan that fails is the use of open ports on the server that have been deemed insecure by your PCI scanning vendor.
In this article we’ll discuss how to use your root access on your server to login with SSH to disable specific open ports on the server that could be causing you to fail a PCI compliance scan. It’s also important to mention that just because your PCI compliance vendor fails your website for an open port, it might not necessarily be an actual security risk, and most will allow you to challenge their initial findings as a false positive.
Common false positives
The following common ports might show up in a failed PCI scan:
- 2082 (cPanel)
- 2083 (cPanel SSL)
- 2086 (WHM – Web Host Manager)
- 2087 (WHM – Web Host Manager SSL)
- 2095 (Webmail)
- 2096 (Webmail SSL)
- 3306 (MySQL Remote Connections)
These ports are used to access the cPanel, WHM, and webmail interfaces from a web-browser. With the last one being for remote MySQL connections. Sometimes leaving the MySQL port open is fine, since you still have to provide a valid user to login to any databases, but it’s up to your PCI vendor’s discretion on if they’ll allow it to be left open.
Closing a port in APF (Advanced Policy Firewall)
Using the steps below we’ll walk you through logging into your server and disabling the remote MySQL port 3306 in your firewall.
- Login to your server via SSH as the root user.
- First make a copy of your apf firewall configration file with the following command:
cp -frp /etc/apf/conf.apf{,.backup}This will create a [/etc/apf/conf.apf.backup] file for you.
- You’ll want to edit the apf firewall configuration file, which can be done with the following command which will use the vim text editor:
vim /etc/apf/conf.apf
When vim is first loaded you’ll be in edit mode, meaning if you type something it doesn’t get inserted into the document.
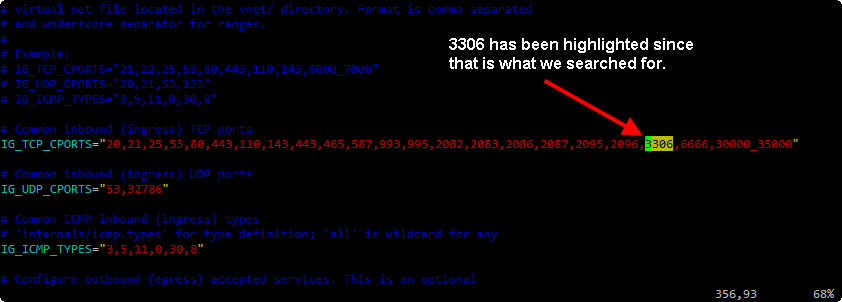
We know that we want to find port 3306 so we type in a forward slash / which is the vim command for find and you’ll notice it drops your cursor to the bottom of the screen and now it allows you to type.
Go ahead and enter 3306 and press Enter and you’ll get dropped to the first instance of 3306 in the file with it highlighted. This is on the IG_TCP_CPORTS line of the firewall configuration which are the common allowed inbound TCP ports.
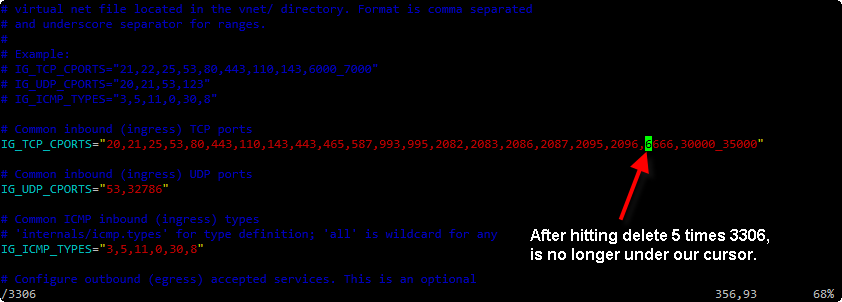
Now because your cursor is right at where 3306 begins you can simply hit the Delete key on your keyboard 5 times, 4 of those will get rid of 3306 and the 5th will get rid of the extra comma left over.
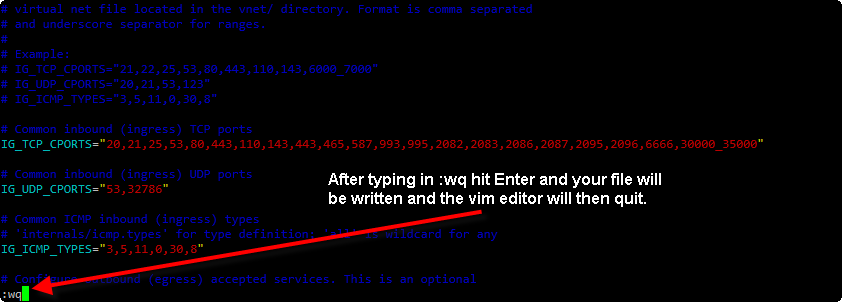
Now hit the colon : key to enter command mode, and type in wq to (w)rite the file and (q)uit the vim editor.
- Now restart the apf firewall service with the following command:
service apf restart
You’ll see a long list of information scroll by and at the end of it you should see:
apf(1734): {glob} default (egress) output accept
apf(1734): {glob} default (ingress) input drop
apf(1673): {glob} firewall initalized
apf(1673): {glob} fast load snapshot savedPort 3306 should now be blocked to the outside world.
You should now know how to disable ports on your server’s firewall to help pass PCI compliance scans. It’s important to note that changing your firewall settings could potentially lock you out of your server if done incorrectly, so please take caution when doing these edits yourself and contact us if you run into any problems.



After numerous attempts to deal with “3306/tcp Possible internet facing database on port 3306″, we discovered that if we use IP whitelisting to prevent any connection from unauthorized IPs, we can dispute the scan results and get the item closed by the scanning company. InMotion Hosting support has been very helpful in assisting us with the IP whitelisting.
Thanks for your comment. Knowing that that is a possibility should help the community and we appreciate you providing that insight!
Hi Jacob,
I am currently trying to figure out how to remove my companys home URL from the PCI Compliance Scan because I only want my subdomain to be scanned. Do you have any insight on the matter?
Hello Ryan,
It isn’t the domain or subdomain that is tested for PCI compliance, but the server that houses the domain. All domains and subdomains will be involved.
Kindest Regards,
Scott M